Configure Slack notifications for backup events
Step 1: Create a Slack app
Go to Slack API apps and create a new Slack app connected to the Oslo kommune workspace. You can choose any name you prefer.
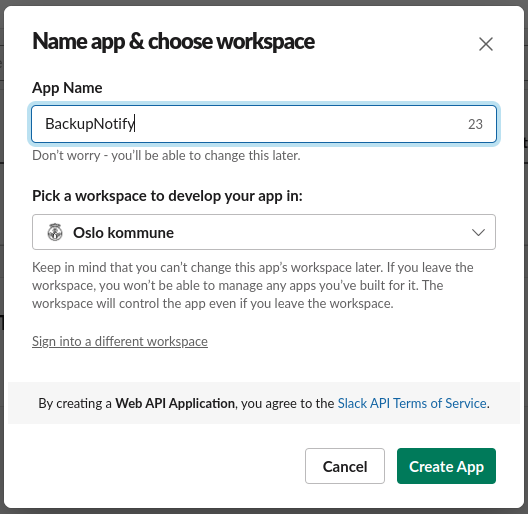
Step 2: Create an incoming Slack webhook
Under Features > Incoming Webhooks activate the toggle incoming webhooks.
Create a new webhook attached to a channel of your choice. Select Add New Webhook to Workspace and select a channel to receive backup notifications in.
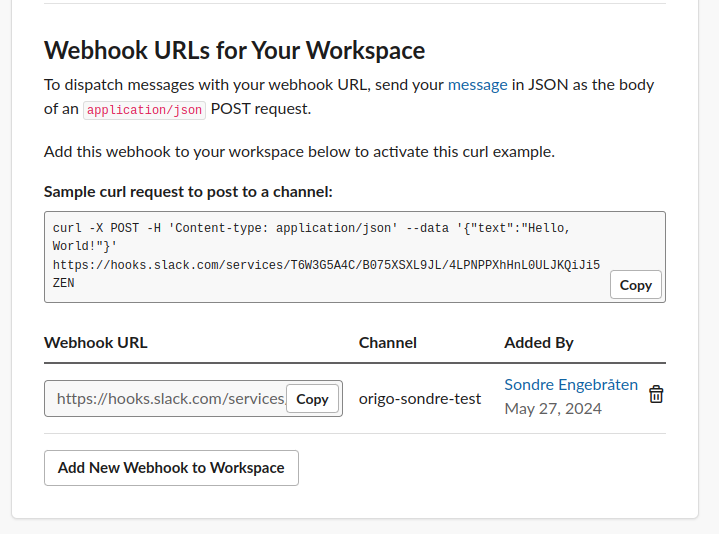
Copy the webhook URL to the clipboard.
Step 3: Set webhook URL in AWS console
In the AWS console, Systems manager > Parameter Store find the SSM Parameter /${local.environment}/slack/webhook/backup. Add the webhook URL from the previous step to this parameter.
Step 4: Configure Slack app name and channel
In your Terraform IaC configuration, locate the file config_override.tf.
Create two new locals like this:
locals{
...
################################################################################
# Slack notifications
################################################################################
slack_username = "reporter"
slack_channel = "temp-aws-root-alerts"
...
}
Adjust Slack username and Slack channel to suit your needs. The Slack channel needs to be the same that you selected in Step #2.
Step 5: Enable Slack notifications
Update vars-backup.yml with the following content:
Step 6: Update the backup stack and apply
Update the stack using Boilerplate:
boilerplate \
--template-url "git@github.com:oslokommune/golden-path-boilerplate.git//boilerplate/terraform/backup?ref=main" \
--var-file vars-backup.yml \
--var-file vars-common.yml \
--output-folder backup \
--non-interactive
Initialize Terraform and apply the configuration:
Step 7: Verify Slack notifications
Next time a backup runs a message should be posted to your channel.
✅ An AWS Backup job was completed successfully
Resource ARN
`arn:aws:rds:eu-west-1:1234567890:cluster:pirates-dev-main`
Recovery point ARN
`arn:aws:rds:eu-west-1:1234567890:cluster-snapshot:awsbackup:job-e09f3a12-9239-7e82-041b-db378838f32e`
Tip
By default you are notified of successful and failed jobs. You can further filter notifications by overriding the backup_vault_events input for the aws_backup module.
Next steps
After 24 hours, follow the guide for enabling immutable backups to verify that the backup is working as expected, and enable immutable backups.